How can PII data be exposed in enterprise AI applications?
Discover how AI systems can accidentally expose personal data through unexpected channels in vector embeddings and unstructured fields, creating privacy risks that traditional security measures can’t catch.
In the first part of this series on Personally Identifiable Information (PII) data, we explored the fundamental importance of protecting sensitive information and its core challenges. As enterprises rapidly adopt AI and data-driven applications to transform their business strategies, they face an emerging and often overlooked threat – Personally Identifiable Information (PII) data exposed through AI systems.
How can organizations protect sensitive data while harnessing the power of these AI advances?
PII exposure risks in AI implementations
As organizations increasingly embed AI and machine learning models into their customer-facing applications, they face unprecedented challenges in protecting Personally Identifiable Information (PII). Modern AI systems process vast amounts of personal data to power features like personalized recommendations, automated customer service, and predictive analytics. However, these advanced capabilities introduce complex privacy risks that traditional security controls weren’t designed to address.
Here are two scenarios where PII exposure risks commonly arise in AI-driven systems:
Vector embeddings and unauthorized API transfers
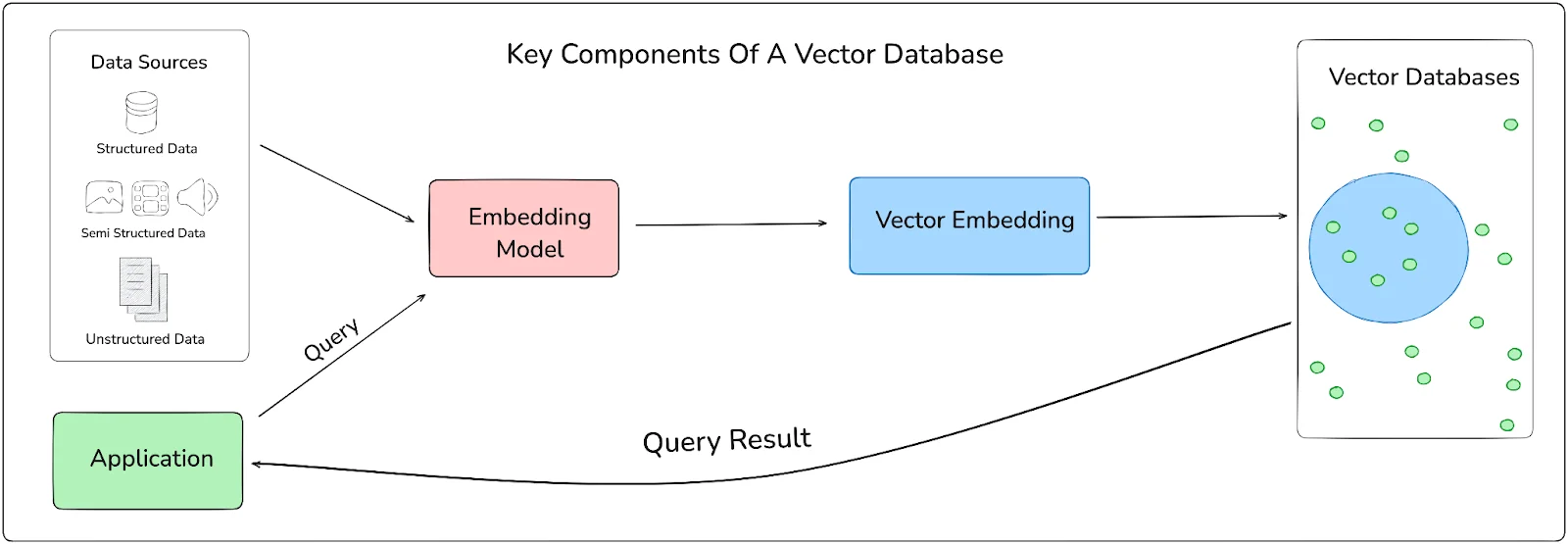
Vector embeddings are numerical data representations that capture semantic information for tasks such as search, recommendation, and conversational AI. These embeddings are created when AI models transform text, user profiles, or behavioral data into fixed-length numerical vectors to understand patterns and similarities. For example, when a recommendation system processes customer purchase history, it converts each transaction and customer attribute into embedding vectors to identify similar customers or predict preferences.
While these embeddings appear abstract numerical vectors, they can preserve identifiable patterns of the original data, especially when generated from sensitive fields like names, addresses, or account details.
This creates two critical exposure risks:
- Data Reconstruction: Vector embeddings can be vulnerable to inversion attacks, where adversarial models reconstruct aspects of the original PII through pattern analysis and inference techniques. For instance, embeddings generated from customer profiles could reveal personal attributes even without direct access to the raw data.
- Unauthorized Transmission: Organizations often unknowingly expose PII when vector embeddings are shared through external APIs or third-party services. Common scenarios include:
- Model serving platforms caching embeddings for performance optimization
- Analytics services logging embedding vectors for debugging
- Integration APIs transmitting embeddings to external systems without proper privacy controls
Undetected PII Exposure in Descriptive Data Fields
Unstructured data fields—like comments, case notes, transaction records, and free-text entries—pose a unique challenge in AI systems. While these fields provide valuable context in CRM systems, support platforms, and data storage environments, they often become inadvertent carriers of sensitive PII. Customer service notes might contain email addresses, support tickets could include account numbers, and transaction descriptions might carry personal details.
The primary concern stems from the lack of systematic controls in handling these unstructured fields. Unlike structured data, where PII can be clearly identified and protected, these free-form fields typically bypass standard protection mechanisms. Organizations struggle to implement consistent PII tagging, access controls, or redaction practices across these fields. The variable nature of how users input information makes it particularly challenging to maintain standardized data protection measures.
This problem compounds as organizations process unstructured data through their AI pipelines. Sensitive information embedded in these fields can flow unchecked into data lakes, becoming accessible through various analytics platforms and BI dashboards. When these data sources feed into AI training datasets, they create a ripple effect of PII exposure.
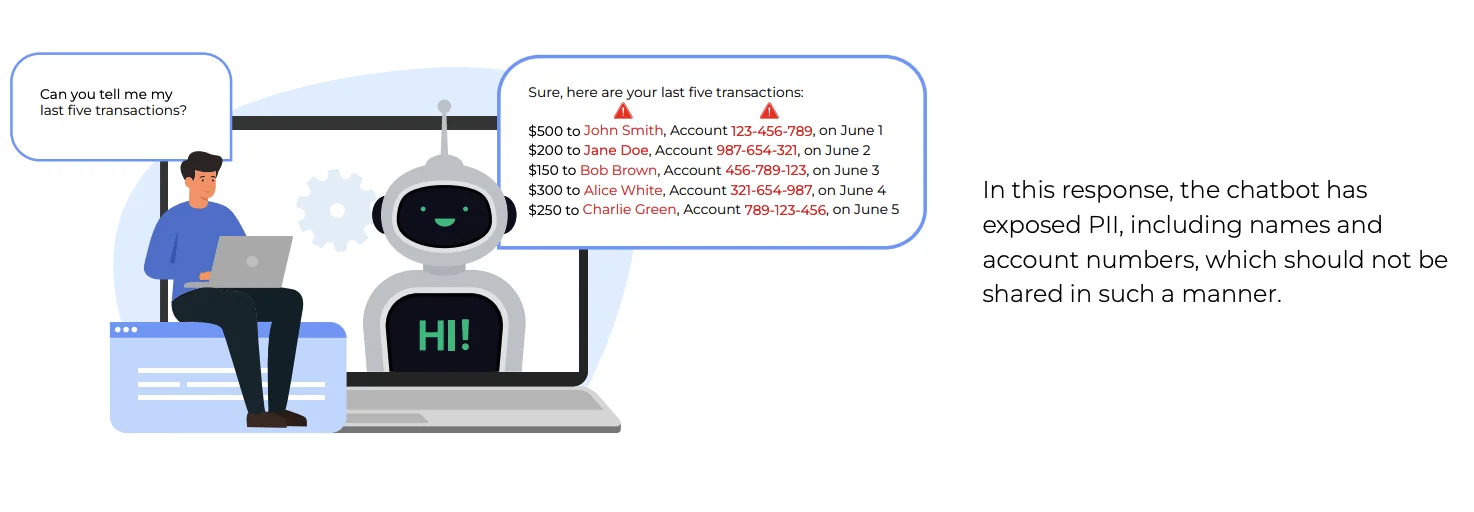
For example, when a customer asks about their transaction history, an AI chatbot might display full names and account numbers in its response without proper masking. Systems log this sensitive data in conversation histories, analytics dashboards, and model training datasets. When developers use these logs to train future versions of the chatbot, the model learns to expose PII in similar conversations, creating a cycle of unintended data exposure.
Traditional tools designed for structured data formats struggle with the contextual nature of unstructured fields. Pattern matching algorithms often fail to catch PII hidden within natural language variations, leading to high false-positive rates or missed detections.
The sheer scale of unstructured data in modern organizations makes manual review impractical. The challenge lies not just in identifying PII within these fields but in maintaining consistent protection as this data flows through increasingly complex AI-driven systems. Automated tools must continuously evolve to handle new patterns of PII exposure.
Conclusion
As AI systems continue to evolve, protecting PII becomes increasingly complex yet critically important. Organizations must proactively identify and secure sensitive data before breaches occur. With automated data quality monitoring solutions like Telmai, you can systematically monitor, detect, and manage data quality at scale across your data ecosystem.
Don’t wait for a breach to act. Click here to see how Telmai’s automated PII monitoring can protect your AI systems by continuously detecting and preventing sensitive data exposure.
Passionate about data quality? Get expert insights and guides delivered straight to your inbox – click here to subscribe to our newsletter now.
- On this page
See what’s possible with Telmai
Request a demo to see the full power of Telmai’s data observability tool for yourself.
